What is an identity resolution strategy?
Your customers are likely to interact with your brand using a variety of touch points and devices across their customer journey. For example, a user may interact with an ad seen on Facebook’s mobile app in the discover stage, visit your site on mobile and desktop during the consider stage, then on desktop in the justify stage before finally purchasing off-line.
This means data from the key interaction points is fragmented, both within the analytics platform as well as across touch point databases, such as in CRM, ERP etc…
If you consider advertising platforms, and the loss of 3rd party cookies, this curtails their ability to recognise users across those touch points and devices. Furthermore, there is no link between advertiser conversion activity and your own databases.
This fragmentation impacts the ability to perform whole of journey analysis, such as marketing efficacy analysis. The capability to draw significant insight and data models is severely curtailed and for most simply not possible.
Ultimately the inability to recognise a customer across devices, visits and channels is the single most significant blocker as businesses move to link systems of insight with engagement across cross channel customer experiences.
Strategy
An identity resolution strategy’s goal is simple: to build and maintain the capability to form a cross functional view of the customer. This should not be confused with the mythical Single Customer View (SCV) concept; a term that has been rather overused, poorly understood and led to many a failed project. Rather it is a pragmatic view to solving a complex marketing, sales, and IT problem.
An identity resolution strategy is supported by three key tactics:
- Embed the consideration of identity resolution across functions and executive levels.
- The generation and propagation across platforms and associated databases of unique user identifier keys.
- The identification and implementation of user authentication opportunities across the customer journey and the capture of high confidence user identification data.
An identity resolution strategy sets firm the business’s intention to be customer centric and to embed within its experience design and supporting technology architecture, the capability to consider and action identity resolution. Specifically, the business is looking to understand the customer interactions and develop better value exchanges with its customers. In turn, the business derives value from a high confidence user identity dataset.
Example – how identity resolution works
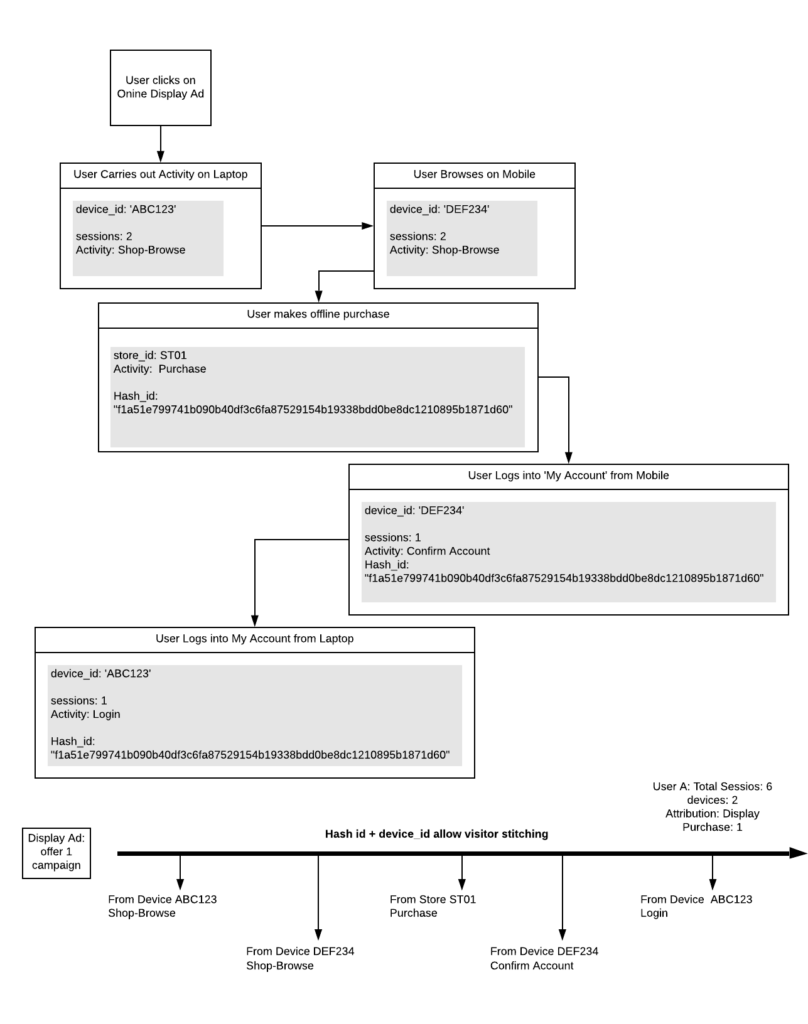
Outcomes
- Activate user identity features in analytics platforms that stitch user interaction across sessions and devices.
- Activate Customer Data Platform (CDP) visitor stitching features to allow audience attribute generation logic for whole of journey and identify specific users for a more personalised experience across touch points.
- Ability to perform cross database stitching, such as combining web activity with CRM or ERP activity for advanced analysis, marketing efficacy reports, segmentation, or other ML data modelling.
- Ability to operationalise insight output with customer experience engagement across customer journey and touchpoints.
Key Identifier Attributes
In addition to primary keys generated by Martech, AdTech and SalesTech platforms, cross journey identity resolution requires at least 2 key data points as secondary keys. These will need to be passed to the data layer in the case of a web or app platform and orchestrated to the platforms in your stack whenever a capture opportunity takes place.
User ID:
- This is an identifier that can be matched to a user.
- A user is said to have identified themselves when for a legitimate reason they provide their email address, or they have logged in and the email address is retrievable at the point of login.
- The email address is unique to the individual making it an ideal identifier. However, the email address is considered PII and its use is restricted under GDPR.
- The email address is therefore encrypted (a hash is generated), normally using one way encryption such as SHA256. This creates a key that is always the same when encrypting but cannot be decrypted to the original email address.
- The hash of the email address can be provided in data layer or the hash can sometimes be performed client side via the TMS. (Tealium iQ offers a built-in crypto extension for this purpose and checkout the CryptoME template for Google Tag Manager (GTM)).
Account Identity:
- This is the CRM account ID for the user, which is normally retrievable at account creation or login.
How to form an identity resolution strategy
Identify touch points
The task here is to form a holistic understanding of how your customers are interacting with your brand, as well which systems are behind these interactions.
I suggest you:
- Map your Customer journey touch points;
- These should be key journey interactions and mapped such that will allow you to identify capture opportunities.
- Map the interactions that are digital or involve human interaction.
- Map the databases / platforms that interact with the user or derive data about the interactions in the customer journey.
- Map interaction processes where a key customer interaction may involve multiple touch points;
- A good example of this is account creation, where a user is normally asked to validate their email.
Capture opportunities
Using the touch point maps you can now assess where your current capture opportunities are, as well as identifying new opportunities to pass a high confidence user ID or encourage a value exchange that leads to an identification.
The earlier you can legitimately encourage a user to identify in the journey and the more they log in, the wider the range of user behaviour that can be associated to the visitor profile and of course is useful in improving your capability to segment between new and existing customers.
The following are some journey touchpoint examples where this may be possible.
- Encouraging an always logged in experience.
- Using 3rd party authentication such as Google, Facebook or other such authentication platforms.
- Creating strong value exchange opportunities to having a site account.
- Gated content;
- This can be less useful if not tied to a verification system prior to the value exchange.
- Passing the user identification key in the email validation link.
Orchestration
Now we have keys and capture opportunities, the business should determine – within the GDPR framework – which platforms to orchestrate the keys to. Remember, GDPR demands that you have documented justifications for the collection and use of the data, with clear outlines of how you intend to process the data.
For more information on setting out an identify resolution strategy or would like assistance doing so, feel free to reach out. We’d be happy to guide you along the way.
 Gavin Attard is a Consultant at 120Feet. An analytics expert who applies over 15 years of commercial and marketing experience across multiple verticals with geek level technical skills in the field of data analytics, digital analytics implementation, target marketing, customer insight and enabling data orchestration for campaign management and personalisation.
Gavin Attard is a Consultant at 120Feet. An analytics expert who applies over 15 years of commercial and marketing experience across multiple verticals with geek level technical skills in the field of data analytics, digital analytics implementation, target marketing, customer insight and enabling data orchestration for campaign management and personalisation.
Alteryx ACE Emeritus and a Tealium Expert, Gavin helps businesses maximise their opportunities by enabling their capability to draw insight and design experiences that drive engagement.

