I have recently spent time with a client revisiting their site cookie opt in configuration. This is something we do regularly, to ensure that the cookie and tag information on the privacy page is up to date and accurate.
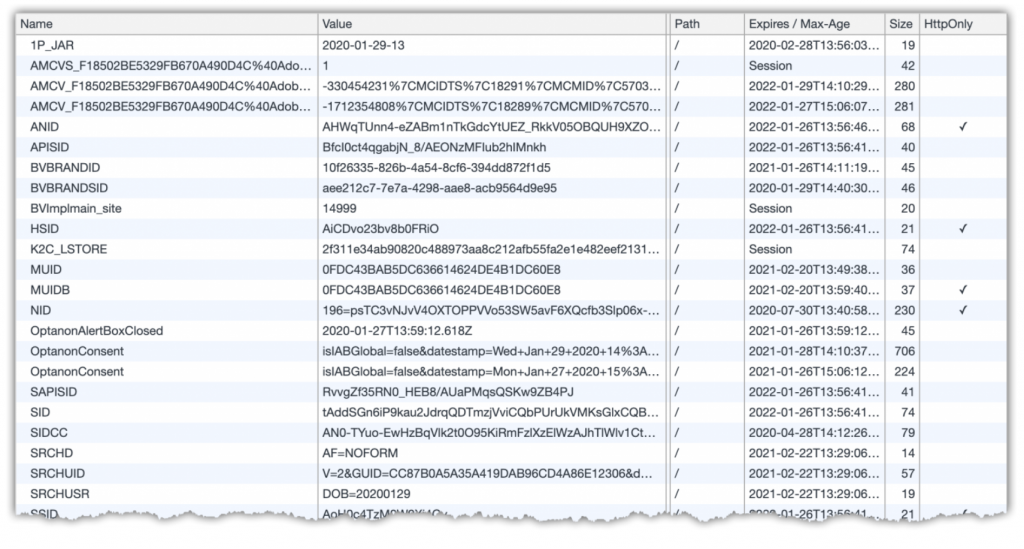
The client in question uses One Trust to perform a scan of the site and then we classify the cookies into four categories, which the customer can then opt in or out of via the [One Trust] banner on the website.
Each time this task comes up (we aim to do it monthly) there are always a few cookies that we have trouble identifying, generally because of an odd name and no indication of the provider. Additionally a lot of cookies these days contain random identifier strings which also offer no clue as to their use of their vendor.
I’ve spent more time than usual this month digging in to where the cookies come from. As most martech and adtech companies seem very reluctant to share what cookies their tools write, I thought it would be useful to share some of the cookies we came across, and what systems they are being used by.
Cookie Name: RT
No clues on this one, just a cookie called RT containing what looks like a URL querystring but with no useful identifiers. After a bit of digging around in the site JS, it looks like this comes from the mPulse beacon (used as a site speed monitoring system), provided by Akamai.
Cookie Name: weird_get_top_level_domain
This cookie looks like something from a dodgy add in or tracker site. After digging around I found some sample code on StackOverflow that uses this cookie to work out what the root level domain for any site is (ie without any subdomains). The JS code tries to write this cookie at each level working backwards through the domain, and as soon as it can be written, that’s the root domain. After some more digging, in the case of our client, this cookie was being written from within the CQuotient site tag. CQuotient is a retail personsalisation solution which was bought by DemandWare (subsequently Salesforce Commerce Cloud). This one is also particularly odd as the OneTrust scan consistently finds it (many times over), but it isn’t listed in the Chrome Application/Cookies panel or in EditThisCookie.
Cookie Names: s_[…] / demdex / everesttech.net
Cookies that start with “s_” are usually internal Adobe Analytics cookies, generally used for storing bits of data between pages or visits. For example, the s_ptc cookie is used for the Performance Timing add in, the s_ppn holds the Previous Page Name, and s_ecid holds the Experience Cloud Visitor ID.
Demdex is the domain that the Experience Cloud Visitor ID Service (formerly Marketing Cloud Visitor ID Service) uses.
Everesttech.net is an Adobe owned advertising exchange platform. The cookies are used to hold the Adobe Advertising Cloud surfer Id and sync subsequent behaviour with the clicked advert.
Cookie Names: _gid / _gat_ / _gcl / sid
These cookies all come from various Google platforms. gid and gat (with or without the underscores – we seemed to have both) are from Google Analytics, gcl and sid are from Google Advertising (Adwords).
Cookie Names: _cs_id / _cs_c / _cs_s
We had a number of cookies stating with _cs, all of which came from Content Square. This is an experience analytics and session replay tool. We use it alongside Adobe to look in more detail at specific journeys and individual user sessions.
Cookie Names: reflow.tv / ctnsnet
These two cookies come from a tool called Scene Stealer. This is a dynamic advertising platform which enables displays ads to be dynamically updated based on the products that the visitor has already seen. The reflow.tv cookie was straightforward to place because this is the domain that the marketing pixel uses but the ctnsnet cookie took a bit more digging to find.
Cookie Names: _scid / sc-static.net / _schn
These cookies come from the Snap Chat retargeting pixel. This pixel is used to retarget and attribute traffic coming from the social network.
Cookie Names: mt.[…]
Monetate is a customer experience optimisation tool. It is used for A/B and MVT testing and for personalisation. It uses multiple cookies as standard, all of which start with “mt.”. We also use an additional one in our implementation to push the experience information from Monetate into Adobe Analytics.
Cookie Names: _px1 / _px2 / _px3 / _pxvid
Perimeter X is a bot protection tool which is used to automatically detect and block traffic which is displaying aggressive bot like behaviour. It writes a number of cookies, all of which use the “px” prefix.
Cookie Name: igodigital
ExactTarget is an email platform that is now run as part of the Salesforce Marketing Cloud. It uses cookies on the site to measure and attribute the impact of email campaigns. Again, the igodigital domain is used by the pixel implemented on the site, so this was straightforward to find. However, it is one that I consistently forget, so have to look it up each time it reappears in the scan.
Investigation methods
The tools I used to investigate these cookies are all in the Chrome browser dev tools.
The first step is to search for the cookie name (alongside “what uses” and “cookie” in the term) and see if Google comes up with anything. Which it generally doesn’t. The one exception here was the Google Analtyics cookie, which is mentioned in one of their help documents.
The next step is to look in the Chrome Network tab. Use the filter to see if the name of the cookie can be found in any of the URLs. This is how cookies such as the igodigital or ctnsnet can be identified. You many need to follow the trail of initiators back to get to the TMS code that fired the initial code, then you can check the code and find out which tag it came from.
The final step is to use the Chrome Search function. This will search through all the files downloaded as part of the page request, including all the JS that is loaded by third parties. The search panel is open by default; you can click on the three dot menu, then click Search. The results contain the scripts or components that include the text; clicking on it will open the file in the sources window and then you will usually have to dig into it to work out if it is using the cookie name. Use the “prettify” button at the bottom of the sources window to make this easier (the button looks like an open and closed curly bracket: {} ).
I hope this article will help you get to the bottom of identifying all the tricky cookies that your site may use. Feel free to comment with any other tricky or odd cookies that you’ve come across.
Ben Stephenson has worked as a consultant for 120Feet for four years. He has ten years of development experience on ecommerce websites, and five years of digital marketing experience as an ecommerce manager looking after a large multinational collection of websites for a Travel and Tourism company. In his spare time he plays guitar, builds with Lego and takes photos (sometimes featuring the guitar or the Lego).